This post explains how to use a vRA Software Component in vRA to implement a generated VM password (local user within Guest OS) and then display it to the user as part of a VM request.
Firstly, create a Software Component or edit an existing one. Add a “Computed” property named “LocalAdminPassword” (or whatever name you prefer). Enter the relevant below code (Bash for Linux or PowerShell for Windows) in the “Configure” life cycle action.
Bash (for Linux VMs):
########## BEGIN: Set password for 'root' ########## ## Generate a password 12 characters long LocalAdminPassword=$(pwgen 12 1 -cn) ## Change root password and set to not expire chage -I -1 -m 0 -M 99999 -E -1 root &> /dev/null echo "root:$LocalAdminPassword" | sudo chpasswd &> /dev/null passwd -e root &> /dev/null echo "Configured 'root' User" ########## END: Set password for 'root' ##########
PowerShell (for Windows VMs):
########## BEGIN: Functions ##########
function Generate-Password {
Param(
[Parameter(Mandatory=$true, Position=0)]
[int] $passwordlength,
[Parameter(Mandatory=$true, Position=1)]
[int] $minspecial
)
## Need a seed as Get-Random isn't always random when inside a loop!
function Get-Seed {
$randombytes=New-Object -typename 'System.Byte[]' 4
$random=New-Object -Typename 'System.Security.Cryptography.RNGCryptoServiceProvider'
$random.getbytes($Randombytes)
[Bitconverter]::ToInt32($Randombytes,0)
}
$password=""
$passwordchars=@('abcdefghijklmnopqrstuvxyz','ABCDEFGHIJKLMNOPQRSTUVWXYZ','0123456789','!^#*')
$passwordgroupchecks=@(0,0,0,0)
## Need to ensure we use all 4 character groups
for ($i=0; $i -lt $passwordlength ;$i++) {
$passwordgroup=Get-Random -minimum 0 -maximum ($passwordgroupchecks.count ) -setseed (Get-Random)
## Before we get to the end of the password, lets check if all the groups have been used
if ($i -gt ($passwordlength - $passwordgroupchecks.count) ) {
$j=0
:groupcheck foreach ($passwordgroupcheck in $passwordgroupchecks) {
if ($passwordgroupcheck -eq 0 ) {
$passwordgroup=$j
break groupcheck
}
$j++
}
## Force special character
if ($passwordgroupchecks[3] -lt $minspecial -and $i -lt ($passwordlength - $minspecial)) {$passwordgroup=3}
}
$chars=$passwordchars[$passwordgroup]
$char=$chars[(Get-Random -minimum 0 -maximum $chars.length -setseed (Get-Seed))]
$passwordgroupchecks[$passwordgroup]+=1
$password+=$char
}
return $password
}
########## END: Functions ##########
########## BEGIN: Set password for 'administrator' ##########
## Generate a password 12 characters long with a special character
$LocalAdminPassword = Generate-Password 12 1
## Use PowerShell cmdlets (where possible) if PS version is 5.1 and above else use 'net user' and 'wmic'
if ($PSVersionTable.PSVersion.Major -ge 5 -And $PSVersionTable.PSVersion.Minor -ge 1) {
$securepass = ConvertTo-SecureString $LocalAdminPassword -AsPlainText -Force
Set-LocalUser -Name "administrator" -Password $securepass -PasswordNeverExpires $false
net user administrator /logonpasswordchg:yes
} else {
net user administrator $InitialPassword
WMIC USERACCOUNT WHERE "Name='administrator'" SET PasswordExpires=TRUE
net user administrator /logonpasswordchg:yes
}
Write-Output "Configured 'Administrator' User"
########## END: Set password for 'administrator' ##########
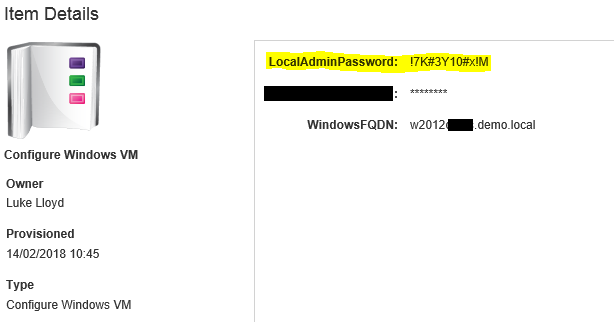
Assign the Software Component in a blueprint. Request the VM build and once built under the Software Component you will see the “LocalAdminPassword” property populated with the generated password.
Nice content Luke.
thanks ?